Access Control and Authorization
Access control is essential for information security, ensuring only authorized users can access specific resources. This section covers Managing User Access, Access Control for Third-Party Tools and Integrations, and Auditing and Monitoring Access.
Key access control principles include:
-
Least Privilege: Limiting user access to the minimum required for their job function.
-
Separation of Duties: Dividing critical tasks among multiple users to prevent fraud or abuse.
-
Need-to-Know: Granting access only to information necessary for a user's role.
Access control ensures that sensitive data is only accessible to authorized users. By implementing Role-Based Access Control (RBAC), the risk of unauthorized access, data breaches and identify theft is minimized. RBAC grants access based on predefined roles and permissions, providing assurance and compliance to data protection laws and regulations like GDPR, LGPD etc. This system upholds user privacy and simultaneously shields the organization's reputation by ensuring robust data protection.
Managing User Access
By default, predefined roles have no access to view PII sensitive field data. Each role should be granted permissions based on the principles of least privilege and need-to-know, ensuring that users have the minimum access necessary to perform their job functions while minimizing the risk of unauthorized access or data breaches. To configure users for access to PII data, you need to modify user roles in Web Administration. You can also configure roles in the Desktop Client - for more information, see Configuring and Setting Up PII Fields.
Note: You must enable PII before modifying roles for access to PII.
To modify a role for access to PII in Web Admin:
This configuration is available only if the PII feature is enabled. For more information, see Enabling PII in Web Administration.
-
Navigate to Security > Roles to display the Roles page.
-
To edit, double-click the role or hover over the role and click the pencil icon on the right.
-
From the General tab:
-
To grant access to PII, check the option to Allow viewing sensitive PII field data.
-
To revoke access to PII, remove the check from the option to Allow viewing sensitive PII field data.
-
-
Click Save
 to save your changes. Please be aware that to enact the changes to the role permissions, users will need to log out, then log back into the system.
to save your changes. Please be aware that to enact the changes to the role permissions, users will need to log out, then log back into the system.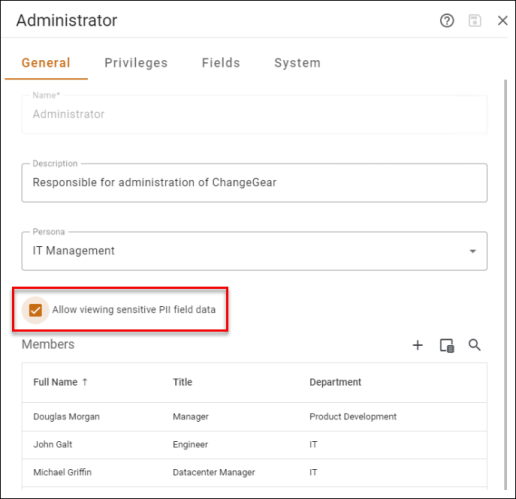
Access Control for Third-Party Tools and Integrations
The REST API provides a secure and efficient way for third-party tools (e.g, Jira, TFS) to access and handle PII. Users will need to use the REST API to make a GET request to the REST API endpoint.
Note: All interactions with the REST API to access PII data are recorded in the PII Audit Log.
-
To access the PII within an Incident Request, you can make a GET request using the third-party tool to the following URL: http://localhost/cgrestapi/api/entity/IncidentRequest/{OID}. Replace {OID} with the OID of the specific Incident Request you want to retrieve.
Note: You can use any HTTP client library or tool to make this request.
-
After making a GET request to the API endpoint, the third-party tool will receive a JSON object containing the details of the Incident Request. This JSON object contains information pertinent to the incident, including PII. The response data you receive depends on your role privileges.
-
If you have access to view PII, you can view PII sensitive data within a ticket.
-
If you have a role that does not have access to sensitive PII data and attempt to access, ChangeGear returns the ticket without any sensitive PII fields in it.
-
For more information on using the Rest API, see Using the REST API > Endpoints and Resources > Entity API > Retrieve Multiple Items.
Auditing and Monitoring Access
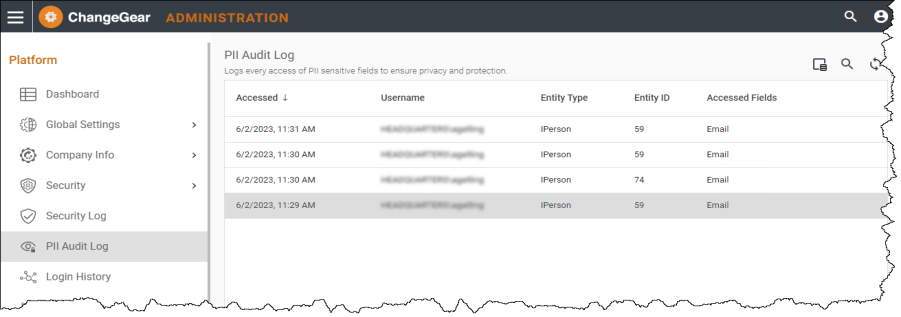
Audit logs help monitor and track user access, activities, and any potential unauthorized actions related to data and resources. The PII Audit Log records all user access to view PII sensitive data. . Using Repository Management, you can create new policy and define data retention periods for PII audit logs and history records. See the Repository Management topic for instructions for how to add a new policy.
To view the PII Audit Log
-
In ChangeGear Web, navigate to the Administration tab.
-
Under the Platform node, click the PII Audit Log to view PII access history.